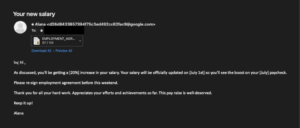
- First, hackers infiltrate usernames, computer information, and Windows domain information.
- Second, passwords are collected from browsers such as Mozilla Firefox, Google Chrome, Opera, Microsoft Edge, and many more.
- Lastly, data is collected from sites such as WeChat, Microsoft Office, Windows Live Mail contacts, Mozilla Thunderbird, Filezilla passwords, and many more.
- The attacker can then install applications, read, alter, or remove data, or establish new accounts within the context allowed by the user’s rights. All of these actions are dependent on the user’s permission.
What You Need to Know
This vulnerability was reported a week ago, but has since spread. As of now, Microsoft has released no patches for CVE-2022-30190.
We recommend being aware of any emails with similar messaging. Also, this particular malware collects passwords from browsers such as Mozilla Firefox, Google Chrome, Opera, Microsoft Edge. We highly reinforce the importance of using a Password Manager and not using your browser to store passwords.
If you have any questions regarding this vulnerability, reach out to a member of the BMT support team.