Catch-IT: Chrome Users, Update Now!
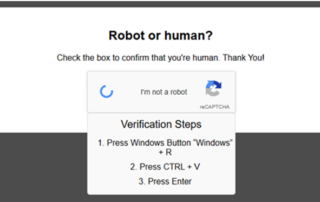
A new zero-day vulnerability (CVE-2025-2783) in Google Chrome is being actively exploited in the wild. This serious flaw lets attackers bypass Chrome's sandbox and potentially run malicious code without user interaction. Researchers indicated “infection occurred immediately after the victim clicked on a link in a phishing email, and the [...]