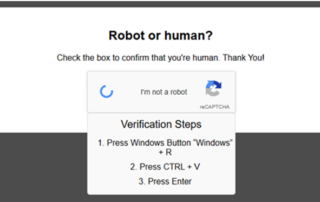
Using SEO and Local Search Optimization to Boost Small Business Sales
Would you describe your small business as having a strong digital presence? Almost everyone looks for what they need online before visiting a store or office. You’re nowhere if it isn’t your business listing that pops up when they click “Search.” Mastering SEO and local search optimization can solve [...]