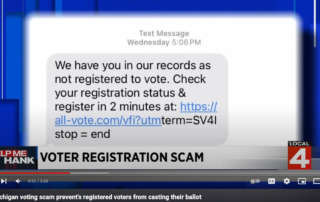
WhatsApp for Windows Security Flaw
Suppose your company uses the popular messaging platform WhatsApp for Windows. In that case, you need to be aware of a potentially critical security flaw that puts your company at risk for a disruptive and costly breach. Users discovered the flaw in June 2024. It allows certain risky file [...]