Chinese Actor SecShow Conducts Massive DNS Probing on Global Scale
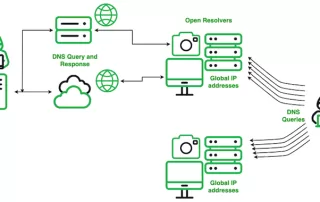
Cybersecurity researchers have shed more light on a Chinese actor codenamed SecShow that has been observed conducting Domain Name System (DNS) on a global scale since at least June 2023. The adversary, according to Infoblox security researchers Dr. Renée Burton and Dave Mitchell, operates from the China Education and [...]