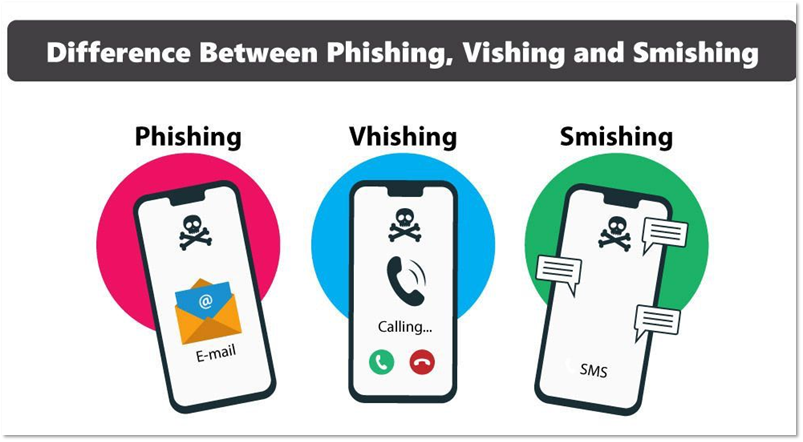
 Vishing, Whaling, SMiShing…what do these things have in common? Although seemingly tied to nautical terms, they are all common phishing tactics. Phishing is a type of social engineering attack that uses email, phone, social media, and other means of personal communication to trick people into providing sensitive information. So, what does these fishy terms mean?
Vishing, Whaling, SMiShing…what do these things have in common? Although seemingly tied to nautical terms, they are all common phishing tactics. Phishing is a type of social engineering attack that uses email, phone, social media, and other means of personal communication to trick people into providing sensitive information. So, what does these fishy terms mean?
Vishing
A is a form of phishing that takes place over the phone. The scammer calls claiming to be a trustworthy entity, attempting to convince the target to provide sensitive personal information. A typical example is an attacker disguising themselves as an organization’s help desk technician or an external technical specialist to gain access to your devices.
Whaling
Whaling targets high-ranking members of an organization by creating a personalized email that appears to be from a legitimate source.
This type of attack requires research about the targeted individual. Then, the attacker uses the details they’ve gathered to craft a sophisticated email that will grab the target’s attention. The goal is to get the business executive or manager to reveal sensitive information, install malware, or transfer funds.
SMiShing
SMiShing or SMS-phishing is conducted through SMS text messages. The attacker sends a text message containing a link to a website of interest, or a request for the target to perform a task or provide sensitive information. SMiShing attacks can also be used to install malware on the target’s device.
What You Should Do
- Never click on links or open attachments delivered with unexpected or unsolicited emails, social media messages, or text messages.
- Use your antivirus software to run a full scan of your system.
- If you provided personal information, monitor your bank accounts, credit profile, and other online accounts for any irregularities or suspicious behavior.
- If you receive a suspicious email from a company where you regularly do business, call the business and forward the email to them to verify the legitimacy of the email.
- Do not reply to spam emails as this only verifies to the sender that your email account is active. Instead, delete the email.
- Use up-to-date antivirus software and firewall protection to prevent and block phishing attacks, and enable multi-factor authentication (MFA) for all accounts that offer it to greatly reduce the risk of your accounts becoming compromised.
- One of the most effective ways to prevent incidents resulting from phishing attacks is through employee training and awareness.







Leave A Comment