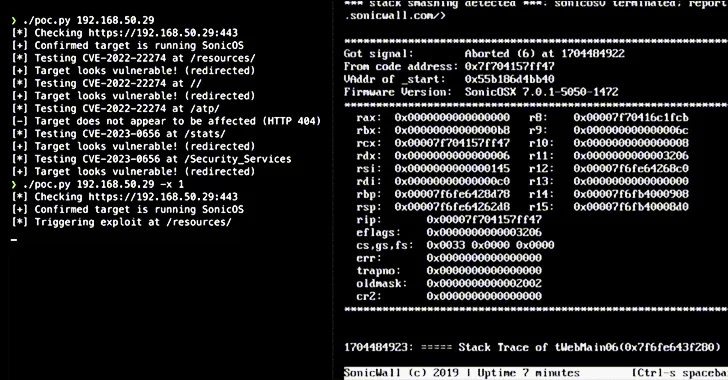
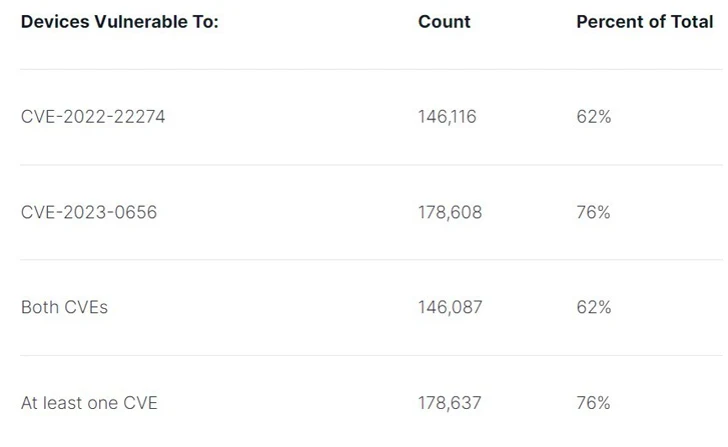
Over 178,000 SonicWall firewalls exposed over the internet are exploitable to at least one of the two security flaws that could be potentially exploited to cause a denial-of-service (DoS) condition and remote code execution (RCE).
“The two issues are fundamentally the same but exploitable at different HTTP URI paths due to reuse of a vulnerable code pattern,” Jon Williams, a senior security engineer at Bishop Fox, said in a technical analysis shared with The Hacker News.
The vulnerabilities in question are listed below –
- CVE-2022-22274 (CVSS score: 9.4) – A stack-based buffer overflow vulnerability in the SonicOS via HTTP request allows a remote, unauthenticated attacker to cause DoS or potentially result in code execution in the firewall.
- CVE-2023-0656 (CVSS score: 7.5) – A stack-based buffer overflow vulnerability in the SonicOS allows a remote, unauthenticated attacker to cause DoS, which could result in a crash.
While there are no reports of exploitation of the flaws in the wild, a proof-of-concept (PoC) for CVE-2023-0656 was published by the SSD Secure Disclosure team April 2023.
The cybersecurity firm revealed that the issues could be weaponized by bad actors to trigger repeated crashes and force the appliance to get into maintenance mode, requiring administrative action to restore normal functionality.
“Perhaps most astonishing was the discovery that over 146,000 publicly-accessible devices are vulnerable to a bug that was published almost two years ago,” Williams said.
The development comes as watchTowr Labs uncovered multiple stack-based buffer overflow flaws in the SonicOS management web interface and SSL VPN portal that could lead to a firewall crash.
To safeguard against possible threats, it’s recommended to update to the last version and ensure that the management interface isn’t exposed to the internet.